mirror of
https://github.com/a0rtega/pafish
synced 2024-11-22 06:11:18 +03:00
29 lines
995 B
Markdown
29 lines
995 B
Markdown
|
|
<img alt="pafish-logo" src="pafish/pafish.ico" align="left" width="64px">
|
|
|
|
# Pafish
|
|
|
|
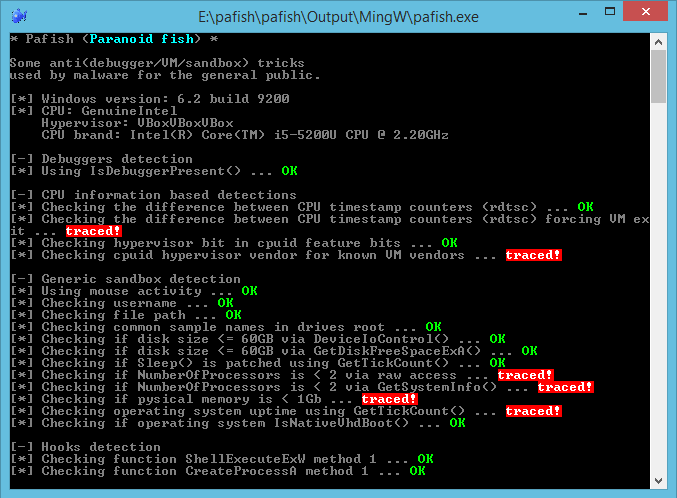
Pafish is a demonstration tool that employs several techniques to detect sandboxes and analysis environments in the same way as malware families do.
|
|
|
|
The project is open source, you can read the code of all anti-analysis checks. You can also **[download](https://github.com/a0rtega/pafish/raw/master/pafish.exe)** the executable of the latest stable version.
|
|
|
|
|
|
|
|
# Scope
|
|
|
|
The objective of this project is to collect usual tricks seen in malware samples. This allows us to study them, and test if our analysis environments are properly implemented.
|
|
|
|
# Build
|
|
|
|
Pafish is written in C and can be built with MinGW (gcc + make).
|
|
|
|
Check out "[How to build](https://github.com/a0rtega/pafish/wiki/How-to-build)" for detailed instructions.
|
|
|
|
# Author
|
|
|
|
Alberto Ortega
|
|
|
|
# License
|
|
|
|
[GPL-3.0](LICENSE.txt)
|