mirror of
https://github.com/a0rtega/pafish
synced 2024-11-24 15:19:36 +03:00
| .github | ||
| pafish | ||
| screenshots | ||
| .gitignore | ||
| CHANGELOG | ||
| LICENSE.txt | ||
| README.md | ||
| Vagrantfile | ||

Pafish
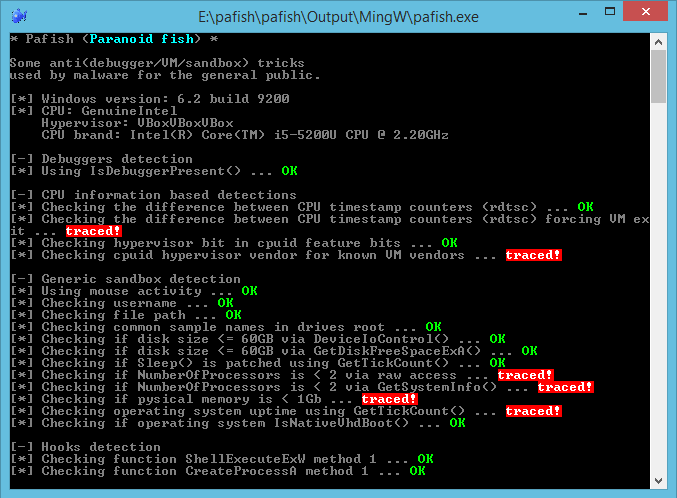
Pafish is a demonstration tool that employs several techniques to detect sandboxes and analysis environments in the same way as malware families do.
The project is open source, you can read the code of all anti-analysis checks. You can also download the executable of the latest stable version.
Scope
The objective of this project is to collect usual tricks seen in malware samples. This allows us to study them, and test if our analysis environments are properly implemented.
Build
Pafish is written in C and can be built with MinGW (gcc + make).
Check out "How to build" for detailed instructions.
Author
Alberto Ortega